Products
ADVANCED NETWORK SECURITY MONITORING, ANALYSIS AND WARNING SYSTEM
Background
Network security is facing unprecedented challenges, mainly from unknown attacks and threats which continuoously impact organization, specific targets. This kind of attack is called APT(Advanced Persistent Threat)or “Attack for Specific Targets”.
It is generally believed that APT is a kind of specific attack that performs a series of attack behaviors in order to obtain important information of an organization or even a country. By using a variety of
attack methods, including the most advanced method and social engineering methodology, APT has gained the permissions from the organization step by step. It tends to make use of insiders of the organization as a springboard for attack. Sometimes the attacker will write special attacking programs for the attacked target, rather than using some common attack code.
Introduction
The system use advanced technical architecture, monitor and intercept customers’ network to discover abnormal network behavior, new attack behavior, spread of unknown malicious code. System can also monitor local website persistently, identify network vulnerabilities, web page Trojans. System can collect external threaten intelligence in real-time, then combine these intelligence with attack behavior, malicious code and network vulnerabilities to make a whole picture for administrator and management, and help them to understand network security situation. Powerful visible presentation function to present attack behavior, real-time warning, and show different analysis statistics and report to user.
Architecture
The system architecture is shown below:
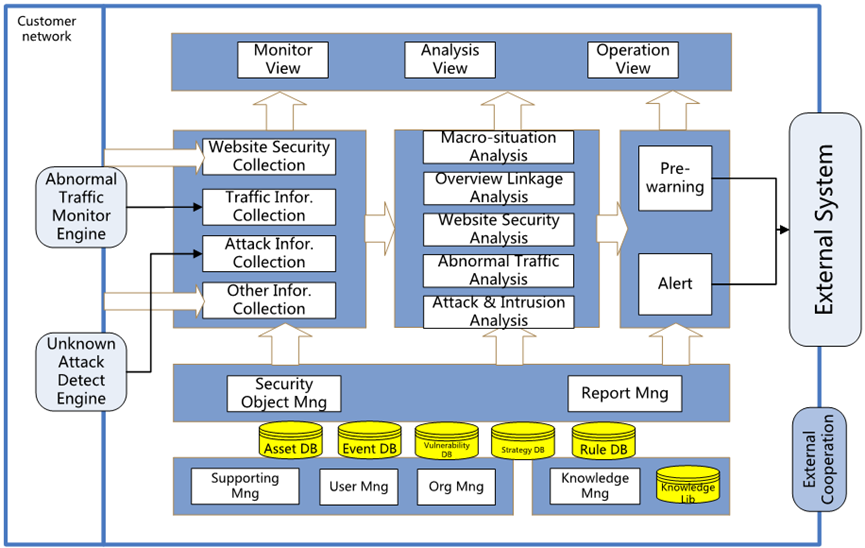
System is composed of six components: Monitor Engine, Information Collector, Information Analyzer, Security Action, User Presentation and System Supporting.
Monitor Engine
Monitor Engine will implant into user network in passive mode, intercept network traffic in real-time, identify suspicious behavior, and then generate internal messages.
Information Collector.
Information Collector collects security information, such as security object information, attack information, network traffic information, and website security information etc. Monitor Engine will provide information of attack behavior and network traffic. And Information Collector can collect network security information from customers’ network without Monitor Engine.
Information Analyzer
Base on all information collected, system can analysis network attack event, abnormal traffic, security of website, overview linkage and macro-situation.
Security Action
Security Action include pre-warning and alert functions.
User Presentation
System provides different user interface for users of different levels or roles. Presenting data is from monitor, analysis & maintenance sections. Users can also customize presentation view according to their particular demand.
System Supporting
System Supporting includes Security Object Management, Report Management, System Management, Privilege Management, Level Management, Knowledge Management and Globe Security Information Library.
Background
Network security is facing unprecedented challenges, mainly from unknown attacks and threats which continuoously impact organization, specific targets. This kind of attack is called APT(Advanced Persistent Threat)or “Attack for Specific Targets”.
It is generally believed that APT is a kind of specific attack that performs a series of attack behaviors in order to obtain important information of an organization or even a country. By using a variety of
attack methods, including the most advanced method and social engineering methodology, APT has gained the permissions from the organization step by step. It tends to make use of insiders of the organization as a springboard for attack. Sometimes the attacker will write special attacking programs for the attacked target, rather than using some common attack code.
The system use advanced technical architecture, monitor and intercept customers’ network to discover abnormal network behavior, new attack behavior, spread of unknown malicious code. System can also monitor local website persistently, identify network vulnerabilities, web page Trojans. System can collect external threaten intelligence in real-time, then combine these intelligence with attack behavior, malicious code and network vulnerabilities to make a whole picture for administrator and management, and help them to understand network security situation. Powerful visible presentation function to present attack behavior, real-time warning, and show different analysis statistics and report to user.
Architecture
The system architecture is shown below:

System is composed of six components: Monitor Engine, Information Collector, Information Analyzer, Security Action, User Presentation and System Supporting.
Monitor Engine
Monitor Engine will implant into user network in passive mode, intercept network traffic in real-time, identify suspicious behavior, and then generate internal messages.
Information Collector.
Information Collector collects security information, such as security object information, attack information, network traffic information, and website security information etc. Monitor Engine will provide information of attack behavior and network traffic. And Information Collector can collect network security information from customers’ network without Monitor Engine.
Information Analyzer
Base on all information collected, system can analysis network attack event, abnormal traffic, security of website, overview linkage and macro-situation.
Security Action
Security Action include pre-warning and alert functions.
User Presentation
System provides different user interface for users of different levels or roles. Presenting data is from monitor, analysis & maintenance sections. Users can also customize presentation view according to their particular demand.
System Supporting
System Supporting includes Security Object Management, Report Management, System Management, Privilege Management, Level Management, Knowledge Management and Globe Security Information Library.

